regedit.exe
- File Path:
C:\Windows\regedit.exe - Description: Registry Editor
Screenshot
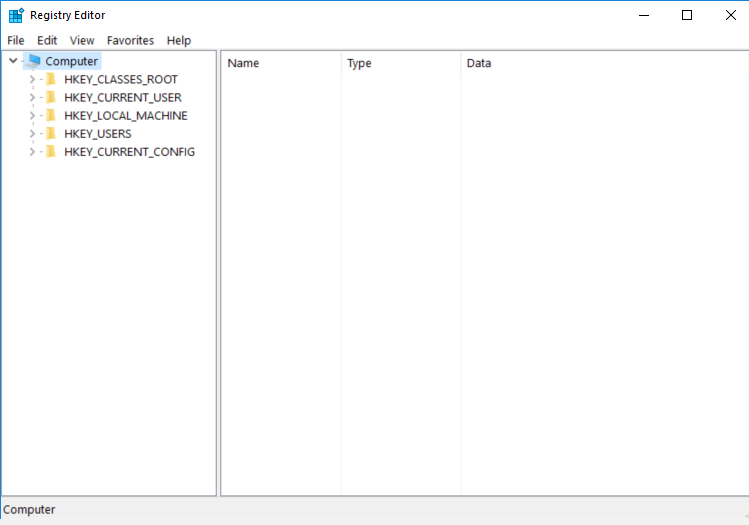
Hashes
| Type | Hash |
|---|---|
| MD5 | A3668018735B59050AD123A5A8CDC184 |
| SHA1 | 1D72449F04F2287A31A91024FC3E3ADA33322E72 |
| SHA256 | FF3B56204F0CEA172AEFB178E05A32C3C3C0BE93F29DD4C2DF46A6DE07BB5152 |
| SHA384 | 25096F9DDF40C883DEF467A2224EC2B739B74AEAE5B540F1CEFB37D5BEC31F885D4F3AC95642B8CC3579E22164C05AF4 |
| SHA512 | CB39E0A4F7C50A449DC113F4B61AB6EF2DCAEBA12170D04DA97A2644D8399CF51F217C84C608DEDD3F35B73F8BBAA1F3F7FDD1EA51AD293BF18BCE2FA38A2C0F |
| SSDEEP | 6144:6qoAOc6qKhTsywE2KBiBQRZ66z+n4VZbd8g79pgrXNgRnVLjyzhbkidNN2:6qvOFhg5KIQRZ66z24VZbdrpgrXN2LWr |
| IMP | 7FEBF576192E34BDF7D07877CBACC413 |
| PESHA1 | 8A502B83863552735A48AFEBF00F967FA7F06CF8 |
| PE256 | C09538DF5350AC6F798E8633280E353DFA3B06EB5E1FBF18A52F5F2A5E484FCF |
Runtime Data
Window Title:
Registry Editor
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\en-US\regedit.exe.mui | File |
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (R-D) C:\Windows\System32\en-US\aclui.dll.mui | File |
| (R-D) C:\Windows\System32\en-US\duser.dll.mui | File |
| (R-D) C:\Windows\System32\en-US\imageres.dll.mui | File |
| (R-D) C:\Windows\WinSxS\amd64_microsoft.windows.c..-controls.resources_6595b64144ccf1df_6.0.17763.1518_en-us_f47974b57ff45754\comctl32.dll.mui | File |
| (RW-) C:\Users\user | File |
| (RW-) C:\Windows\WinSxS\amd64_microsoft.windows.c..-controls.resources_6595b64144ccf1df_6.0.17763.1518_en-us_f47974b57ff45754 | File |
| (RW-) C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17763.1518_none_de6e2bd0534e2567 | File |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*cversions.2.ro | Section |
| \BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \Sessions\2\Windows\Theme2131664586 | Section |
| \Windows\Theme966197582 | Section |
Loaded Modules:
| Path |
|---|
| C:\Windows\regedit.exe |
| C:\Windows\SYSTEM32\ACLUI.dll |
| C:\Windows\System32\ADVAPI32.dll |
| C:\Windows\SYSTEM32\AUTHZ.dll |
| C:\Windows\System32\bcryptPrimitives.dll |
| C:\Windows\System32\cfgmgr32.dll |
| C:\Windows\SYSTEM32\clb.dll |
| C:\Windows\System32\combase.dll |
| C:\Windows\System32\COMDLG32.dll |
| C:\Windows\System32\cryptsp.dll |
| C:\Windows\System32\GDI32.dll |
| C:\Windows\System32\gdi32full.dll |
| C:\Windows\System32\IMM32.DLL |
| C:\Windows\System32\kernel.appcore.dll |
| C:\Windows\System32\KERNEL32.DLL |
| C:\Windows\System32\KERNELBASE.dll |
| C:\Windows\System32\msvcp_win.dll |
| C:\Windows\System32\msvcrt.dll |
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\SYSTEM32\NTDSAPI.dll |
| C:\Windows\System32\ole32.dll |
| C:\Windows\System32\OLEAUT32.dll |
| C:\Windows\System32\powrprof.dll |
| C:\Windows\System32\profapi.dll |
| C:\Windows\System32\RPCRT4.dll |
| C:\Windows\System32\sechost.dll |
| C:\Windows\System32\shcore.dll |
| C:\Windows\System32\SHELL32.dll |
| C:\Windows\System32\SHLWAPI.dll |
| C:\Windows\System32\ucrtbase.dll |
| C:\Windows\SYSTEM32\ulib.dll |
| C:\Windows\System32\USER32.dll |
| C:\Windows\SYSTEM32\UxTheme.dll |
| C:\Windows\System32\win32u.dll |
| C:\Windows\System32\windows.storage.dll |
| C:\Windows\System32\WS2_32.dll |
| C:\Windows\SYSTEM32\XmlLite.dll |
| C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17763.1518_none_de6e2bd0534e2567\COMCTL32.dll |
Signature
- Status: Signature verified.
- Serial:
3300000266BD1580EFA75CD6D3000000000266 - Thumbprint:
A4341B9FD50FB9964283220A36A1EF6F6FAA7840 - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: REGEDIT.EXE.MUI
- Product Name: Microsoft Windows Operating System
- Company Name: Microsoft Corporation
- File Version: 10.0.17763.1 (WinBuild.160101.0800)
- Product Version: 10.0.17763.1
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 64-bit
File Scan
- VirusTotal Detections: 0/71
- VirusTotal Link: https://www.virustotal.com/gui/file/ff3b56204f0cea172aefb178e05a32c3c3c0be93f29dd4c2df46a6de07bb5152/detection/
File Similarity (ssdeep match)
Possible Misuse
The following table contains possible examples of regedit.exe being misused. While regedit.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | sysmon_regedit_export_to_ads.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Regedit.yml |
DRL 1.0 |
| sigma | sysmon_regedit_export_to_ads.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| sigma | proc_creation_win_alternate_data_streams.yml | - 'regedit ' |
DRL 1.0 |
| sigma | proc_creation_win_regedit_export_critical_keys.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Regedit.yml |
DRL 1.0 |
| sigma | proc_creation_win_regedit_export_critical_keys.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| sigma | proc_creation_win_regedit_export_keys.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Regedit.yml |
DRL 1.0 |
| sigma | proc_creation_win_regedit_export_keys.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys.yml | description: Detects the import of the specified file to the registry with regedit.exe. |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Regedit.yml |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys_ads.yml | description: Detects the import of a alternate datastream to the registry with regedit.exe. |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys_ads.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Regedit.yml |
DRL 1.0 |
| sigma | proc_creation_win_regedit_import_keys_ads.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_regedit_trustedinstaller.yml | title: Regedit as Trusted Installer |
DRL 1.0 |
| sigma | proc_creation_win_susp_regedit_trustedinstaller.yml | description: Detects a regedit started with TrustedInstaller privileges or by ProcessHacker.exe |
DRL 1.0 |
| sigma | proc_creation_win_susp_regedit_trustedinstaller.yml | Image\|endswith: '\regedit.exe' |
DRL 1.0 |
| LOLBAS | Regedit.yml | Name: Regedit.exe |
|
| LOLBAS | Regedit.yml | - Command: regedit /E c:\ads\file.txt:regfile.reg HKEY_CURRENT_USER\MyCustomRegKey |
|
| LOLBAS | Regedit.yml | - Command: regedit C:\ads\file.txt:regfile.reg |
|
| LOLBAS | Regedit.yml | - Path: C:\Windows\System32\regedit.exe |
|
| LOLBAS | Regedit.yml | - Path: C:\Windows\SysWOW64\regedit.exe |
|
| LOLBAS | Regedit.yml | - IOC: regedit.exe reading and writing to alternate data stream |
|
| LOLBAS | Regedit.yml | - IOC: regedit.exe should normally not be executed by end-users |
|
| malware-ioc | misp_invisimole.json | "description": "Masquerading occurs when the name or location of an executable, legitimate or malicious, is manipulated or abused for the sake of evading defenses and observation. Several different variations of this technique have been observed.\n\nOne variant is for an executable to be placed in a commonly trusted directory or given the name of a legitimate, trusted program. Alternatively, the filename given may be a close approximation of legitimate programs or something innocuous. An example of this is when a common system utility or program is moved and renamed to avoid detection based on its usage.(Citation: FireEye APT10 Sept 2018) This is done to bypass tools that trust executables by relying on file name or path, as well as to deceive defenders and system administrators into thinking a file is benign by associating the name with something that is thought to be legitimate.\n\nA third variant uses the right-to-left override (RTLO or RLO) character (U+202E) as a means of tricking a user into executing what they think is a benign file type but is actually executable code. RTLO is a non-printing character that causes the text that follows it to be displayed in reverse.(Citation: Infosecinstitute RTLO Technique) For example, a Windows screensaver file named <code>March 25 \\u202Excod.scr</code> will display as <code>March 25 rcs.docx</code>. A JavaScript file named <code>photo_high_re\\u202Egnp.js</code> will be displayed as <code>photo_high_resj.png</code>. A common use of this technique is with spearphishing attachments since it can trick both end users and defenders if they are not aware of how their tools display and render the RTLO character. Use of the RTLO character has been seen in many targeted intrusion attempts and criminal activity.(Citation: Trend Micro PLEAD RTLO)(Citation: Kaspersky RTLO Cyber Crime) RTLO can be used in the Windows Registry as well, where regedit.exe displays the reversed characters but the command line tool reg.exe does not by default. \n\nAdversaries may modify a binary's metadata, including such fields as icons, version, name of the product, description, and copyright, to better blend in with the environment and increase chances of deceiving a security analyst or product.(Citation: Threatexpress MetaTwin 2017)\n\n### Windows\nIn another variation of this technique, an adversary may use a renamed copy of a legitimate utility, such as rundll32.exe. (Citation: Endgame Masquerade Ball) An alternative case occurs when a legitimate utility is moved to a different directory and also renamed to avoid detections based on system utilities executing from non-standard paths. (Citation: F-Secure CozyDuke)\n\nAn example of abuse of trusted locations in Windows would be the <code>C:\\Windows\\System32</code> directory. Examples of trusted binary names that can be given to malicious binares include \"explorer.exe\" and \"svchost.exe\".\n\n### Linux\nAnother variation of this technique includes malicious binaries changing the name of their running process to that of a trusted or benign process, after they have been launched as opposed to before. (Citation: Remaiten)\n\nAn example of abuse of trusted locations in Linux would be the <code>/bin</code> directory. Examples of trusted binary names that can be given to malicious binaries include \"rsyncd\" and \"dbus-inotifier\". (Citation: Fysbis Palo Alto Analysis) (Citation: Fysbis Dr Web Analysis)", |
© ESET 2014-2018 |
| malware-ioc | rtm | regedit.exe |
© ESET 2014-2018 |
| atomic-red-team | T1564.004.md | regedit /E #{path}\file.txt:regfile.reg HKEY_CURRENT_USER\MyCustomRegKey | MIT License. © 2018 Red Canary |
| signature-base | apt_area1_phishing_diplomacy.yar | $regedit = { c7 06 23 01 12 20 c7 46 04 01 90 00 00 89 5e 0c 89 5e 08 e8 | CC BY-NC 4.0 |
| signature-base | apt_project_sauron_extras.yar | $x1 = “local t = w.exec2str("regedit “ | CC BY-NC 4.0 |
| signature-base | crime_cn_campaign_njrat.yar | $a4 = “taskkill /f /im regedit.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_recon_indicators.yar | $s9 = “regedit -e “ ascii | CC BY-NC 4.0 |
MIT License. Copyright (c) 2020-2021 Strontic.