InfDefaultInstall.exe
- File Path:
C:\WINDOWS\SysWOW64\InfDefaultInstall.exe - Description: INF Default Install
Screenshot
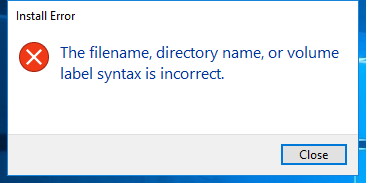
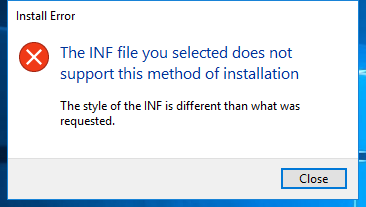
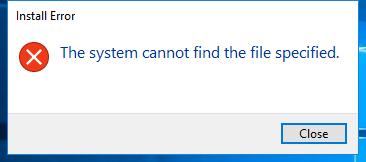
Hashes
| Type | Hash |
|---|---|
| MD5 | 310F6C1B3B98576F84C2ABC567260B00 |
| SHA1 | 3275F9FA8CE225DF8C5BC6469BF149F5416BBF34 |
| SHA256 | 8425CEF86C050BF8F7E78DAC0BFAB8ABCB9AE69C27E14C4CBC212F9BB20BD2D1 |
| SHA384 | 6F8DCF820E8369E96DABD8ADA0BBA8A56697D4F549DB35C8A4A353FEF13B138D0E4FE6C41CA3255265C69C8987392A96 |
| SHA512 | C9D732CED7D45ECE8B18B3D253266A9F2E41D57FDA92C893C818BFBAF68979874283D5AEBFEDA9A2CB93EA56D6DFFC8DD7F99C1EF12D16CECD1132E57DA7E38A |
| SSDEEP | 192:B0M7tRFkRmkhKV4RY6EwgPx4sZKW/GWs:B0cFomkIV4lGx4oKW/GWs |
| IMP | F2F450CE56A210FAE3C67AF46756BF51 |
| PESHA1 | 14EBD89E35B00D00CBA44B6A7B3ECB785E97D234 |
| PE256 | 5A3127E7CD54BE00C8FA8DD8BC2993EDACFC5A74EA625B4666C1646383E71F4A |
Runtime Data
Loaded Modules:
| Path |
|---|
| C:\WINDOWS\SYSTEM32\ntdll.dll |
| C:\WINDOWS\System32\wow64.dll |
| C:\WINDOWS\System32\wow64base.dll |
| C:\WINDOWS\System32\wow64con.dll |
| C:\WINDOWS\System32\wow64cpu.dll |
| C:\WINDOWS\System32\wow64win.dll |
| C:\WINDOWS\SysWOW64\InfDefaultInstall.exe |
Signature
- Status: Signature verified.
- Serial:
33000002ED2C45E4C145CF48440000000002ED - Thumbprint:
312860D2047EB81F8F58C29FF19ECDB4C634CF6A - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: InfDefaultInstall.EXE
- Product Name: Microsoft Windows Operating System
- Company Name: Microsoft Corporation
- File Version: 5.2.3668.0
- Product Version: 5.2.3668.0
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 32-bit
File Scan
- VirusTotal Detections: 0/73
- VirusTotal Link: https://www.virustotal.com/gui/file/8425cef86c050bf8f7e78dac0bfab8abcb9ae69c27e14c4cbc212f9bb20bd2d1/detection
File Similarity (ssdeep match)
| File | Score |
|---|---|
| C:\Windows\SysWOW64\InfDefaultInstall.exe | 35 |
| C:\WINDOWS\SysWOW64\InfDefaultInstall.exe | 32 |
| C:\Windows\SysWOW64\InfDefaultInstall.exe | 32 |
| C:\Windows\SysWOW64\InfDefaultInstall.exe | 35 |
Possible Misuse
The following table contains possible examples of InfDefaultInstall.exe being misused. While InfDefaultInstall.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | proc_creation_win_infdefaultinstall.yml | title: InfDefaultInstall.exe .inf Execution |
DRL 1.0 |
| sigma | proc_creation_win_infdefaultinstall.yml | - https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Infdefaultinstall.yml |
DRL 1.0 |
| sigma | proc_creation_win_infdefaultinstall.yml | - 'InfDefaultInstall.exe ' |
DRL 1.0 |
| LOLBAS | Infdefaultinstall.yml | Name: Infdefaultinstall.exe |
|
| LOLBAS | Infdefaultinstall.yml | - Command: InfDefaultInstall.exe Infdefaultinstall.inf |
|
| LOLBAS | Infdefaultinstall.yml | - Path: C:\Windows\System32\Infdefaultinstall.exe |
|
| LOLBAS | Infdefaultinstall.yml | - Path: C:\Windows\SysWOW64\Infdefaultinstall.exe |
|
| atomic-red-team | index.md | - Atomic Test #4: InfDefaultInstall.exe .inf Execution [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - Atomic Test #4: InfDefaultInstall.exe .inf Execution [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | - Atomic Test #4 - InfDefaultInstall.exe .inf Execution | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | ## Atomic Test #4 - InfDefaultInstall.exe .inf Execution | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | Test execution of a .inf using InfDefaultInstall.exe | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | Reference: https://github.com/LOLBAS-Project/LOLBAS/blob/master/yml/OSBinaries/Infdefaultinstall.yml | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | | inf_to_execute | Local location of inf file | String | PathToAtomicsFolder\T1218\src\Infdefaultinstall.inf| | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | InfDefaultInstall.exe #{inf_to_execute} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.md | Invoke-WebRequest “https://github.com/redcanaryco/atomic-red-team/raw/master/atomics/T1218/src/Infdefaultinstall.inf” -OutFile “#{inf_to_execute}” | MIT License. © 2018 Red Canary |
MIT License. Copyright (c) 2020-2021 Strontic.