setup.exe
- File Path:
C:\Program Files (x86)\Microsoft\Edge\Application\95.0.1020.40\Installer\setup.exe - Description: Microsoft Edge Installer
Screenshot
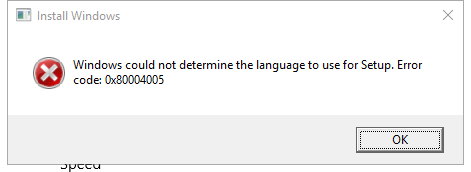
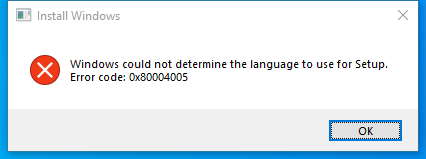
Hashes
| Type | Hash |
|---|---|
| MD5 | 6B5C895FA7F048B343AD9C0687526120 |
| SHA1 | EB9E9C9C267DA03F8AEEAB0CCA30A115A3F7F635 |
| SHA256 | DAC519816B2AC00FE7D8832F2748A4F81B878AF884146B3855110A96766D8A83 |
| SHA384 | E4434A31AD59DDCF3744E79A080E441F41A939AC9F35DEAA593C3DB9402E4429F41DBE9F9F1A55538EBFB0EA90565766 |
| SHA512 | 758E6047F389A624A03718B60B7DCA23DD206B685507966AD838F3E76F8BB7576E1DD9FE5A08FDC97B8A557789C6126032E1379B0348B1880D4F65D980C11A6C |
| SSDEEP | 49152:onTJK0jrjubAFJcvvpXcGxgfEW00ajbvRXu36aJM0iBvp1cNxXpVe:RbXxg34RDhpgX2 |
| IMP | 37C4D5D64884246A378826739AABB73C |
| PESHA1 | 964AD7A2AD35E3D4A691D1F48E2E554E578770FB |
| PE256 | 7E88C8EB5A9A0B61F3E2E1FA6C23CB6B41A70209482903D14CA92EC8E3E450FC |
Runtime Data
Usage (stderr):
[7420:10256:1106/201251.009:7936546:ERROR:setup_main.cc(886)] Already installed version 92.0.902.67 at system-level conflicts with this one at user-level.
[7420:10256:1106/201251.066:7936593:ERROR:persistent_histogram_storage.cc(121)] Could not write "SetupMetrics" persistent histograms to file as the storage directory does not exist.
Child Processes:
msedge.exe
Loaded Modules:
| Path |
|---|
| C:\Program Files (x86)\Microsoft\Edge\Application\95.0.1020.40\Installer\setup.exe |
| C:\Windows\System32\KERNEL32.DLL |
| C:\Windows\System32\KERNELBASE.dll |
| C:\Windows\SYSTEM32\ncrypt.dll |
| C:\Windows\SYSTEM32\NTASN1.dll |
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\System32\RPCRT4.dll |
| C:\Windows\System32\sechost.dll |
Signature
- Status: Signature verified.
- Serial:
33000001E2F17D92020E49F87F0000000001E2 - Thumbprint:
C774204049D25D30AF9AC2F116B3C1FB88EE00A4 - Issuer: CN=Microsoft Code Signing PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: setup.exe
- Product Name: Microsoft Edge Installer
- Company Name: Microsoft Corporation
- File Version: 95.0.1020.40
- Product Version: 95.0.1020.40
- Language: English (United States)
- Legal Copyright: Copyright Microsoft Corporation. All rights reserved.
- Machine Type: 64-bit
File Scan
- VirusTotal Detections: 0/73
- VirusTotal Link: https://www.virustotal.com/gui/file/dac519816b2ac00fe7d8832f2748a4f81b878af884146b3855110a96766d8a83/detection
Possible Misuse
The following table contains possible examples of setup.exe being misused. While setup.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | sigma-test.yml | uses: actions/setup-python@v1 |
DRL 1.0 |
| sigma | aws_update_login_profile.yml | An attacker with the iam:UpdateLoginProfile permission on other users can change the password used to login to the AWS console on any user that already has a login profile setup. |
DRL 1.0 |
| sigma | cisco_cli_net_sniff.yml | description: Show when a monitor or a span/rspan is setup or modified |
DRL 1.0 |
| sigma | cisco_cli_net_sniff.yml | - Admins may setup new or modify old spans, or use a monitor for troubleshooting |
DRL 1.0 |
| sigma | win_iso_mount.yml | ObjectName: '\Device\CdRom0\setup.exe' |
DRL 1.0 |
| sigma | win_susp_eventlog_cleared.yml | - Rollout of log collection agents (the setup routine often includes a reset of the local Eventlog) |
DRL 1.0 |
| sigma | win_system_susp_eventlog_cleared.yml | - Rollout of log collection agents (the setup routine often includes a reset of the local Eventlog) |
DRL 1.0 |
| sigma | file_event_win_cve_2021_31979_cve_2021_33771_exploits.yml | - 'C:\Windows\system32\config\cy-GB\Setup\SKB\InputMethod\TupTask.dat' |
DRL 1.0 |
| sigma | proc_access_win_cred_dump_lsass_access.yml | SourceImage\|endswith: \Installer\setup.exe |
DRL 1.0 |
| sigma | proc_creation_win_apt_winnti_pipemon.yml | - 'setup.exe' |
DRL 1.0 |
| sigma | proc_creation_win_exploit_cve_2019_1378.yml | - 'C:\Windows\Setup\Scripts\' |
DRL 1.0 |
| sigma | proc_creation_win_exploit_cve_2019_1378.yml | - 'C:\Windows\Setup\' |
DRL 1.0 |
| sigma | proc_creation_win_powershell_cmdline_special_characters.yml | - Amazon SSM Document Worker # fp example: powershell " [Console]::OutputEncoding = [System.Text.Encoding]::UTF8 $keyExists = Test-Path "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" $jsonObj = @() if ($keyExists) { $key = Get-Item "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" $valueNames = $key.GetValueNames(); foreach ($valueName in $valueNames) { $value = $key.GetValue($valueName); if ($value -gt 0) { $installed = "True" } else { $installed = "False" } $jsonObj += @" {"Name": "$valueName", "Installed": "$installed"} "@ } } $result = $jsonObj -join "," $result = "[" + $result + "]" [Console]::WriteLine($result) |
DRL 1.0 |
| sigma | proc_creation_win_susp_run_folder.yml | - 'C:\Program Files (x86)\Microsoft Visual Studio\Installer\resources\app\ServiceHub\Services\Microsoft.VisualStudio.Setup.Service\BackgroundDownload.exe' |
DRL 1.0 |
| sigma | proc_creation_win_vmtoolsd_susp_child_process.yml | description: Detects suspicious child process creations of VMware Tools process which may indicate persistence setup |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SYSTEM\Setup\CmdLine' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SYSTEM\Setup\CmdLine' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | TargetObject\|contains: '\SOFTWARE\Microsoft\Active Setup\Installed Components\{8A69D345-D564-463c-AFF1-A69D9E530F96}\' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_wow6432node.yml | - '\setup.exe' |
DRL 1.0 |
| sigma | registry_event_mal_flowcloud.yml | - 'HKLM\SYSTEM\Setup\PrintResponsor\' |
DRL 1.0 |
| sigma | registry_event_new_application_appcompat.yml | - Newly setup system. |
DRL 1.0 |
| sigma | registry_event_runonce_persistence.yml | TargetObject\|startswith: 'HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| LOLBAS | Setup.yml | Name: Setup.exe |
|
| LOLBAS | Setup.yml | - Command: Run Setup.exe |
|
| LOLBAS | Setup.yml | Description: Hijack hpbcsiServiceMarshaller.exe and run Setup.exe to launch a payload. |
|
| LOLBAS | OneDriveStandaloneUpdater.yml | - IOC: Reports of downloading from suspicious URLs in %localappdata%\OneDrive\setup\logs\StandaloneUpdate_*.log files |
|
| LOLBAS | Runonce.yml | - IOC: Registy key add - HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\YOURKEY |
|
| LOLBAS | Setupapi.yml | Description: Windows Setup Application Programming Interface |
|
| LOLBAS | Syssetup.yml | Description: Windows NT System Setup |
|
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-sf |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-nh |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-zn |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-pq |
© ESET 2014-2018 |
| malware-ioc | evilnum | \|C8458A1568639EA2270E1845B0A386FF75C23421\|nvstviews.exe \|ALPS Setup \|B1C248AD370D1ACE6FA03572CE1AE6297E14A3F8``{:.highlight .language-cmhg} |
© ESET 2014-2018 |
| malware-ioc | glupteba.misp-event.json | "value": "setup.exe\|f7230b2cab4e4910bca473b39ee8fd4df394ce0d", |
© ESET 2014-2018 |
| malware-ioc | glupteba | \|F7230B2CAB4E4910BCA473B39EE8FD4DF394CE0D\|setup.exe \|MSIL/Adware.CsdiMonetize.AG |
© ESET 2014-2018 |
| malware-ioc | win_apt_invisimole_wdigest_chain.yml | - Legitimate use of the Wireless Network Setup Wizard |
© ESET 2014-2018 |
| malware-ioc | win_lolbin_setupSNK.yml | title: Wireless Network Setup Settings Changed |
© ESET 2014-2018 |
| malware-ioc | win_lolbin_setupSNK.yml | - Legitimate use of the Wireless Network Setup Wizard |
© ESET 2014-2018 |
| malware-ioc | misp-kryptocibule.json | "value": "%ProgramFiles(X86)%\\Adobe\\Acrobat Reader DC\\Reader\\Update\\Setup.dll", |
© ESET 2014-2018 |
| malware-ioc | misp-kryptocibule.json | "value": "%ProgramFiles(X86)%\\Adobe\\Acrobat Reader DC\\Reader\\Update\\setup-version.json", |
© ESET 2014-2018 |
| malware-ioc | kryptocibule | %ProgramFiles(X86)%\Adobe\Acrobat Reader DC\Reader\Update\Setup.dll |
© ESET 2014-2018 |
| malware-ioc | kryptocibule | %ProgramFiles(X86)%\Adobe\Acrobat Reader DC\Reader\Update\setup-version.json |
© ESET 2014-2018 |
| malware-ioc | potao | Fake TrueCrypt Setup: |
© ESET 2014-2018 |
| malware-ioc | 2021_T2 | Setup |
© ESET 2014-2018 |
| malware-ioc | windigo | depending on your setup. For example we know that suPHP uses shared memory. |
© ESET 2014-2018 |
| malware-ioc | winnti_group | setup.exe |
© ESET 2014-2018 |
| atomic-red-team | index.md | - T1547.014 Active Setup CONTRIBUTE A TEST | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - T1547.014 Active Setup CONTRIBUTE A TEST | MIT License. © 2018 Red Canary |
| atomic-red-team | matrix.md | | Compromise Software Dependencies and Development Tools CONTRIBUTE A TEST | At (Windows) | Active Setup CONTRIBUTE A TEST | Accessibility Features | Application Access Token CONTRIBUTE A TEST | AS-REP Roasting | Browser Bookmark Discovery | Distributed Component Object Model | Archive via Custom Method CONTRIBUTE A TEST | Exfiltration Over Alternative Protocol | Bidirectional Communication CONTRIBUTE A TEST | Application or System Exploitation CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | matrix.md | | Compromise Software Supply Chain CONTRIBUTE A TEST | Command and Scripting Interpreter CONTRIBUTE A TEST | Add Office 365 Global Administrator Role CONTRIBUTE A TEST | Active Setup CONTRIBUTE A TEST | Asynchronous Procedure Call | Bash History | Cloud Account CONTRIBUTE A TEST | Exploitation of Remote Services CONTRIBUTE A TEST | Archive via Library | Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | Commonly Used Port CONTRIBUTE A TEST | Data Destruction | | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-matrix.md | | Compromise Software Supply Chain CONTRIBUTE A TEST | Component Object Model CONTRIBUTE A TEST | Active Setup CONTRIBUTE A TEST | Accessibility Features | Asynchronous Procedure Call | Brute Force CONTRIBUTE A TEST | Browser Bookmark Discovery | Exploitation of Remote Services CONTRIBUTE A TEST | Archive via Custom Method CONTRIBUTE A TEST | Exfiltration Over Alternative Protocol | Bidirectional Communication CONTRIBUTE A TEST | Application or System Exploitation CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-matrix.md | | Default Accounts | Component Object Model and Distributed COM CONTRIBUTE A TEST | Add-ins | Active Setup CONTRIBUTE A TEST | BITS Jobs | Cached Domain Credentials CONTRIBUTE A TEST | Domain Account | Internal Spearphishing CONTRIBUTE A TEST | Archive via Library CONTRIBUTE A TEST | Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | Commonly Used Port CONTRIBUTE A TEST | Data Destruction | | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | | nmap_url | NMap installer download URL | Url | https://nmap.org/dist/nmap-7.80-setup.exe| | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | Invoke-WebRequest -OutFile $env:temp\nmap-7.80-setup.exe #{nmap_url} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | Start-Process $env:temp\nmap-7.80-setup.exe /S | MIT License. © 2018 Red Canary |
| atomic-red-team | T1047.md | Invoke-WebRequest ‘https://www.tightvnc.com/download/2.8.63/tightvnc-2.8.63-gpl-setup-64bit.msi’ -OutFile PathToAtomicsFolder\T1047\bin\tightvncinstaller.msi | MIT License. © 2018 Red Canary |
| atomic-red-team | T1484.002.md | if ($new) { Write-Host “nFederation successfully added to Azure AD" } else { Write-Host "nThe federation setup failed” } |
MIT License. © 2018 Red Canary |
| signature-base | airbnb_binaryalert.yar | $a1 = “https://setup.icloud.com/setup/authenticate/” wide ascii | CC BY-NC 4.0 |
| signature-base | airbnb_binaryalert.yar | $s8 = “Setup a communication socket with the process by injecting” fullword ascii wide | CC BY-NC 4.0 |
| signature-base | apt_bluetermite_emdivi.yar | $x1 = “Setup=unsecess.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_bluetermite_emdivi.yar | $x2 = “Setup=leassnp.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_irontiger.yar | $s0 = “\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_irontiger.yar | $s3 = “setup.exeUT” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_miniasp.yar | $x2 = “run http://%s/logo.png setup.exe” fullword ascii /* PEStudio Blacklist: strings / / score: ‘37.02’ */ | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $x1 = “cmd /c expand %TEMP%\setup.cab -F:* %SystemRoot%\System32” | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $x2 = “del /f /q %TEMP%\setup.cab && cliconfg.exe” | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $s6 = “\setup.cab” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_promethium_neodymium.yar | $s2 = “c:\windows\temp\TrueCrypt-Setup-7.1a-tamindir.exe” fullword wide | CC BY-NC 4.0 |
| signature-base | apt_sakula.yar | description = “Sakula shellcode - taken from decoded setup.msi but may not be unique enough to identify Sakula” | CC BY-NC 4.0 |
| signature-base | apt_threatgroup_3390.yar | $s7 = “setup.exeUT” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_threatgroup_3390.yar | $s6 = “\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_winnti_burning_umbrella.yar | $s1 = “c:\windows\ime\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | description = “Sample from CN Honker Pentest Toolset - file setup.exe” | CC BY-NC 4.0 |
| signature-base | crime_fireball.yar | $s3 = “\SETUP.dll” fullword wide | CC BY-NC 4.0 |
| signature-base | crime_nopetya_jun17.yar | $x6 = “wevtutil cl Setup & wevtutil cl System” ascii | CC BY-NC 4.0 |
| signature-base | gen_anomalies_keyword_combos.yar | $fp6 = “Paint.NET Setup” wide fullword | CC BY-NC 4.0 |
| signature-base | gen_cn_hacktools.yar | $s2 = “SwitchSniffer Setup” fullword wide | CC BY-NC 4.0 |
MIT License. Copyright (c) 2020-2021 Strontic.