dialer.exe
- File Path:
C:\Windows\SysWOW64\dialer.exe - Description: Microsoft Windows Phone Dialer
Screenshot
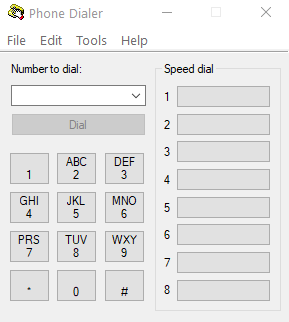
Hashes
| Type | Hash |
|---|---|
| MD5 | 4467865D2CD15FDA91C9D64758A9BAFE |
| SHA1 | C789DB914C3DFD64440235E1C0A315B66C002134 |
| SHA256 | 366857DE6E835CA6A12E33503F6726A2E8528E7F1F9AC74435E2A6BD3C3ED481 |
| SHA384 | A3B5206E049751F194F272D3FA4A4B6769EDC5E28A2A1A7F0705CC156FBDA404E31749AB4AB714C105DA5023DAC3F1B4 |
| SHA512 | A99BBD09F1E50AC8D2C6DBD26791354BBC1BD8AE9655E7D43793A7D3EAADF7AD49F0A64E0A898622B527B7963B3BAA23EF4DF1FB05885298DFE265A59836AFAB |
| SSDEEP | 384:tBp25iPnE6e9vGoH+WWjOMd213y1CaUgDgkK384jLhMFVRLg4R81dULWtUKWjdXz:tG5xMoHCjbd213+Ugk70P+1dU/dv |
| IMP | 76E0D8D65462216E7B0903BC27D606D1 |
| PESHA1 | 4C1946B2584FBBFED2A7820F32BBB5D0AC999408 |
| PE256 | 62DF8B532A02F469B82D43E0A99E93916AC8D25DFFFA68CFD1370DA88BAA9249 |
Runtime Data
Window Title:
Phone Dialer
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (R-D) C:\Windows\System32\en-US\imageres.dll.mui | File |
| (R-D) C:\Windows\SysWOW64\en-US\dialer.exe.mui | File |
| (R-D) C:\Windows\SysWOW64\en-US\user32.dll.mui | File |
| (RW-) C:\Users\user | File |
| (RW-) C:\Windows | File |
| (RW-) C:\Windows\WinSxS\x86_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17763.1518_none_261b62a767ca4e6d | File |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*cversions.2.ro | Section |
| \BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \Sessions\2\Windows\Theme2131664586 | Section |
| \Windows\Theme966197582 | Section |
Loaded Modules:
| Path |
|---|
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\System32\wow64.dll |
| C:\Windows\System32\wow64cpu.dll |
| C:\Windows\System32\wow64win.dll |
| C:\Windows\SysWOW64\dialer.exe |
Signature
- Status: Signature verified.
- Serial:
33000001C422B2F79B793DACB20000000001C4 - Thumbprint:
AE9C1AE54763822EEC42474983D8B635116C8452 - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: DIALER.EXE.MUI
- Product Name: Microsoft Windows Operating System
- Company Name: Microsoft Corporation
- File Version: 10.0.17763.1 (WinBuild.160101.0800)
- Product Version: 10.0.17763.1
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 32-bit
File Scan
- VirusTotal Detections: 0/70
- VirusTotal Link: https://www.virustotal.com/gui/file/366857de6e835ca6a12e33503f6726a2e8528e7f1f9ac74435e2a6bd3c3ed481/detection/
Possible Misuse
The following table contains possible examples of dialer.exe being misused. While dialer.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| LOLBAS | Rasautou.yml | Description: Windows Remote Access Dialer |
MIT License. Copyright (c) 2020-2021 Strontic.