Setup.exe
- File Path:
C:\Windows\system32\oobe\Setup.exe - Description: Windows Installation and Setup
Screenshot
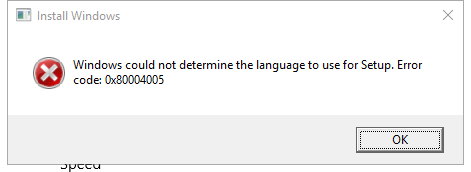
Hashes
| Type | Hash |
|---|---|
| MD5 | 8BBDBD0FA1F6AD661B85FC8A5BD3E2B3 |
| SHA1 | 97FEDC6701284EA05E45B91B4D2066B48B36A212 |
| SHA256 | 6600EEFF725DA15CD3C7D5D10E1F1ABA79FEFE47F4D3CA490E36A45249DC0B23 |
| SHA384 | 061725D1E72DDC15CF8907A357ABE305C213E3C314773E995EB68B638648CFD2BE93DD6D19ED704D007E44083DEAA7C1 |
| SHA512 | F9706A280CCB54F57A3764BC797855CE2275E15C888041D86DD49323F81B9E4FF10B6CC5E7048B6E9EAACB79DBEA6CC9AD81979F8D9B0B7C0CA024C01A64CA6D |
| SSDEEP | 6144:yQkCRcNHLceEUQkAtEKbRsknK+zhQXJgzBU4GfFSc:yQkCONHLtEU6KtYagc |
Signature
- Status: Signature verified.
- Serial:
3300000266BD1580EFA75CD6D3000000000266 - Thumbprint:
A4341B9FD50FB9964283220A36A1EF6F6FAA7840 - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
File Metadata
- Original Filename: SETUP.EXE.MUI
- Product Name: Microsoft Windows Operating System
- Company Name: Microsoft Corporation
- File Version: 10.0.14393.0 (rs1_release.160715-1616)
- Product Version: 10.0.14393.0
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
File Similarity (ssdeep match)
Possible Misuse
The following table contains possible examples of Setup.exe being misused. While Setup.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | sigma-test.yml | uses: actions/setup-python@v1 |
DRL 1.0 |
| sigma | aws_update_login_profile.yml | An attacker with the iam:UpdateLoginProfile permission on other users can change the password used to login to the AWS console on any user that already has a login profile setup. |
DRL 1.0 |
| sigma | cisco_cli_net_sniff.yml | description: Show when a monitor or a span/rspan is setup or modified |
DRL 1.0 |
| sigma | cisco_cli_net_sniff.yml | - Admins may setup new or modify old spans, or use a monitor for troubleshooting |
DRL 1.0 |
| sigma | win_iso_mount.yml | ObjectName: '\Device\CdRom0\setup.exe' |
DRL 1.0 |
| sigma | win_susp_eventlog_cleared.yml | - Rollout of log collection agents (the setup routine often includes a reset of the local Eventlog) |
DRL 1.0 |
| sigma | win_system_susp_eventlog_cleared.yml | - Rollout of log collection agents (the setup routine often includes a reset of the local Eventlog) |
DRL 1.0 |
| sigma | file_event_win_cve_2021_31979_cve_2021_33771_exploits.yml | - 'C:\Windows\system32\config\cy-GB\Setup\SKB\InputMethod\TupTask.dat' |
DRL 1.0 |
| sigma | proc_access_win_cred_dump_lsass_access.yml | SourceImage\|endswith: \Installer\setup.exe |
DRL 1.0 |
| sigma | proc_creation_win_apt_winnti_pipemon.yml | - 'setup.exe' |
DRL 1.0 |
| sigma | proc_creation_win_exploit_cve_2019_1378.yml | - 'C:\Windows\Setup\Scripts\' |
DRL 1.0 |
| sigma | proc_creation_win_exploit_cve_2019_1378.yml | - 'C:\Windows\Setup\' |
DRL 1.0 |
| sigma | proc_creation_win_powershell_cmdline_special_characters.yml | - Amazon SSM Document Worker # fp example: powershell " [Console]::OutputEncoding = [System.Text.Encoding]::UTF8 $keyExists = Test-Path "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" $jsonObj = @() if ($keyExists) { $key = Get-Item "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" $valueNames = $key.GetValueNames(); foreach ($valueName in $valueNames) { $value = $key.GetValue($valueName); if ($value -gt 0) { $installed = "True" } else { $installed = "False" } $jsonObj += @" {"Name": "$valueName", "Installed": "$installed"} "@ } } $result = $jsonObj -join "," $result = "[" + $result + "]" [Console]::WriteLine($result) |
DRL 1.0 |
| sigma | proc_creation_win_susp_run_folder.yml | - 'C:\Program Files (x86)\Microsoft Visual Studio\Installer\resources\app\ServiceHub\Services\Microsoft.VisualStudio.Setup.Service\BackgroundDownload.exe' |
DRL 1.0 |
| sigma | proc_creation_win_vmtoolsd_susp_child_process.yml | description: Detects suspicious child process creations of VMware Tools process which may indicate persistence setup |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SYSTEM\Setup\CmdLine' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification.yml | - '\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SYSTEM\Setup\CmdLine' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | - '\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_common.yml | TargetObject\|contains: '\SOFTWARE\Microsoft\Active Setup\Installed Components\{8A69D345-D564-463c-AFF1-A69D9E530F96}\' |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_wow6432node.yml | - '\setup.exe' |
DRL 1.0 |
| sigma | registry_event_mal_flowcloud.yml | - 'HKLM\SYSTEM\Setup\PrintResponsor\' |
DRL 1.0 |
| sigma | registry_event_new_application_appcompat.yml | - Newly setup system. |
DRL 1.0 |
| sigma | registry_event_runonce_persistence.yml | TargetObject\|startswith: 'HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components' |
DRL 1.0 |
| LOLBAS | Setup.yml | Name: Setup.exe |
|
| LOLBAS | Setup.yml | - Command: Run Setup.exe |
|
| LOLBAS | Setup.yml | Description: Hijack hpbcsiServiceMarshaller.exe and run Setup.exe to launch a payload. |
|
| LOLBAS | OneDriveStandaloneUpdater.yml | - IOC: Reports of downloading from suspicious URLs in %localappdata%\OneDrive\setup\logs\StandaloneUpdate_*.log files |
|
| LOLBAS | Runonce.yml | - IOC: Registy key add - HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\YOURKEY |
|
| LOLBAS | Setupapi.yml | Description: Windows Setup Application Programming Interface |
|
| LOLBAS | Syssetup.yml | Description: Windows NT System Setup |
|
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-sf |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-nh |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-zn |
© ESET 2014-2018 |
| malware-ioc | attor | %COMMONAPPDATA%\Adobe\Setup\Replicate\US-pq |
© ESET 2014-2018 |
| malware-ioc | evilnum | \|C8458A1568639EA2270E1845B0A386FF75C23421\|nvstviews.exe \|ALPS Setup \|B1C248AD370D1ACE6FA03572CE1AE6297E14A3F8``{:.highlight .language-cmhg} |
© ESET 2014-2018 |
| malware-ioc | glupteba.misp-event.json | "value": "setup.exe\|f7230b2cab4e4910bca473b39ee8fd4df394ce0d", |
© ESET 2014-2018 |
| malware-ioc | glupteba | \|F7230B2CAB4E4910BCA473B39EE8FD4DF394CE0D\|setup.exe \|MSIL/Adware.CsdiMonetize.AG |
© ESET 2014-2018 |
| malware-ioc | win_apt_invisimole_wdigest_chain.yml | - Legitimate use of the Wireless Network Setup Wizard |
© ESET 2014-2018 |
| malware-ioc | win_lolbin_setupSNK.yml | title: Wireless Network Setup Settings Changed |
© ESET 2014-2018 |
| malware-ioc | win_lolbin_setupSNK.yml | - Legitimate use of the Wireless Network Setup Wizard |
© ESET 2014-2018 |
| malware-ioc | misp-kryptocibule.json | "value": "%ProgramFiles(X86)%\\Adobe\\Acrobat Reader DC\\Reader\\Update\\Setup.dll", |
© ESET 2014-2018 |
| malware-ioc | misp-kryptocibule.json | "value": "%ProgramFiles(X86)%\\Adobe\\Acrobat Reader DC\\Reader\\Update\\setup-version.json", |
© ESET 2014-2018 |
| malware-ioc | kryptocibule | %ProgramFiles(X86)%\Adobe\Acrobat Reader DC\Reader\Update\Setup.dll |
© ESET 2014-2018 |
| malware-ioc | kryptocibule | %ProgramFiles(X86)%\Adobe\Acrobat Reader DC\Reader\Update\setup-version.json |
© ESET 2014-2018 |
| malware-ioc | potao | Fake TrueCrypt Setup: |
© ESET 2014-2018 |
| malware-ioc | 2021_T2 | Setup |
© ESET 2014-2018 |
| malware-ioc | windigo | depending on your setup. For example we know that suPHP uses shared memory. |
© ESET 2014-2018 |
| malware-ioc | winnti_group | setup.exe |
© ESET 2014-2018 |
| atomic-red-team | index.md | - T1547.014 Active Setup CONTRIBUTE A TEST | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | - T1547.014 Active Setup CONTRIBUTE A TEST | MIT License. © 2018 Red Canary |
| atomic-red-team | matrix.md | | Compromise Software Dependencies and Development Tools CONTRIBUTE A TEST | At (Windows) | Active Setup CONTRIBUTE A TEST | Accessibility Features | Application Access Token CONTRIBUTE A TEST | AS-REP Roasting | Browser Bookmark Discovery | Distributed Component Object Model | Archive via Custom Method CONTRIBUTE A TEST | Exfiltration Over Alternative Protocol | Bidirectional Communication CONTRIBUTE A TEST | Application or System Exploitation CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | matrix.md | | Compromise Software Supply Chain CONTRIBUTE A TEST | Command and Scripting Interpreter CONTRIBUTE A TEST | Add Office 365 Global Administrator Role CONTRIBUTE A TEST | Active Setup CONTRIBUTE A TEST | Asynchronous Procedure Call | Bash History | Cloud Account CONTRIBUTE A TEST | Exploitation of Remote Services CONTRIBUTE A TEST | Archive via Library | Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | Commonly Used Port CONTRIBUTE A TEST | Data Destruction | | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-matrix.md | | Compromise Software Supply Chain CONTRIBUTE A TEST | Component Object Model CONTRIBUTE A TEST | Active Setup CONTRIBUTE A TEST | Accessibility Features | Asynchronous Procedure Call | Brute Force CONTRIBUTE A TEST | Browser Bookmark Discovery | Exploitation of Remote Services CONTRIBUTE A TEST | Archive via Custom Method CONTRIBUTE A TEST | Exfiltration Over Alternative Protocol | Bidirectional Communication CONTRIBUTE A TEST | Application or System Exploitation CONTRIBUTE A TEST | | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-matrix.md | | Default Accounts | Component Object Model and Distributed COM CONTRIBUTE A TEST | Add-ins | Active Setup CONTRIBUTE A TEST | BITS Jobs | Cached Domain Credentials CONTRIBUTE A TEST | Domain Account | Internal Spearphishing CONTRIBUTE A TEST | Archive via Library CONTRIBUTE A TEST | Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | Commonly Used Port CONTRIBUTE A TEST | Data Destruction | | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | | nmap_url | NMap installer download URL | Url | https://nmap.org/dist/nmap-7.80-setup.exe| | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | Invoke-WebRequest -OutFile $env:temp\nmap-7.80-setup.exe #{nmap_url} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1046.md | Start-Process $env:temp\nmap-7.80-setup.exe /S | MIT License. © 2018 Red Canary |
| atomic-red-team | T1047.md | Invoke-WebRequest ‘https://www.tightvnc.com/download/2.8.63/tightvnc-2.8.63-gpl-setup-64bit.msi’ -OutFile PathToAtomicsFolder\T1047\bin\tightvncinstaller.msi | MIT License. © 2018 Red Canary |
| atomic-red-team | T1484.002.md | if ($new) { Write-Host “nFederation successfully added to Azure AD" } else { Write-Host "nThe federation setup failed” } |
MIT License. © 2018 Red Canary |
| signature-base | airbnb_binaryalert.yar | $a1 = “https://setup.icloud.com/setup/authenticate/” wide ascii | CC BY-NC 4.0 |
| signature-base | airbnb_binaryalert.yar | $s8 = “Setup a communication socket with the process by injecting” fullword ascii wide | CC BY-NC 4.0 |
| signature-base | apt_bluetermite_emdivi.yar | $x1 = “Setup=unsecess.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_bluetermite_emdivi.yar | $x2 = “Setup=leassnp.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_irontiger.yar | $s0 = “\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_irontiger.yar | $s3 = “setup.exeUT” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_miniasp.yar | $x2 = “run http://%s/logo.png setup.exe” fullword ascii /* PEStudio Blacklist: strings / / score: ‘37.02’ */ | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $x1 = “cmd /c expand %TEMP%\setup.cab -F:* %SystemRoot%\System32” | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $x2 = “del /f /q %TEMP%\setup.cab && cliconfg.exe” | CC BY-NC 4.0 |
| signature-base | apt_op_honeybee.yar | $s6 = “\setup.cab” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_promethium_neodymium.yar | $s2 = “c:\windows\temp\TrueCrypt-Setup-7.1a-tamindir.exe” fullword wide | CC BY-NC 4.0 |
| signature-base | apt_sakula.yar | description = “Sakula shellcode - taken from decoded setup.msi but may not be unique enough to identify Sakula” | CC BY-NC 4.0 |
| signature-base | apt_threatgroup_3390.yar | $s7 = “setup.exeUT” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_threatgroup_3390.yar | $s6 = “\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_winnti_burning_umbrella.yar | $s1 = “c:\windows\ime\setup.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | description = “Sample from CN Honker Pentest Toolset - file setup.exe” | CC BY-NC 4.0 |
| signature-base | crime_fireball.yar | $s3 = “\SETUP.dll” fullword wide | CC BY-NC 4.0 |
| signature-base | crime_nopetya_jun17.yar | $x6 = “wevtutil cl Setup & wevtutil cl System” ascii | CC BY-NC 4.0 |
| signature-base | gen_anomalies_keyword_combos.yar | $fp6 = “Paint.NET Setup” wide fullword | CC BY-NC 4.0 |
| signature-base | gen_cn_hacktools.yar | $s2 = “SwitchSniffer Setup” fullword wide | CC BY-NC 4.0 |
MIT License. Copyright (c) 2020-2021 Strontic.