Everything.exe
- File Path:
C:\program files\Everything\Everything.exe - Description: Everything
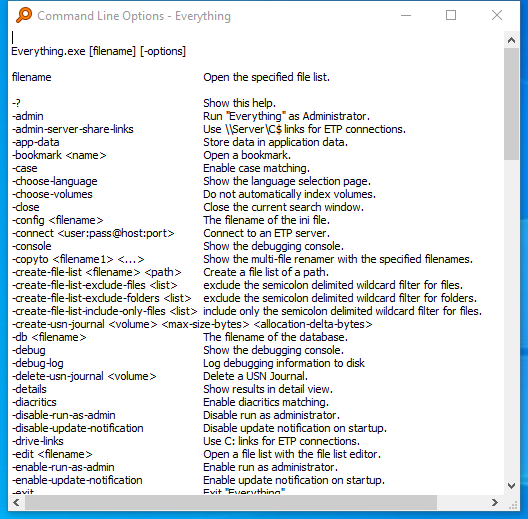
Screenshot
Hashes
| Type | Hash |
|---|---|
| MD5 | 462FB57AD469C670E93EE05CAD1D9DE9 |
| SHA1 | 57916930EA9C4C062E431D58FE68C5749FE1C410 |
| SHA256 | A8E8A69C6ADBDEE716B58D3768E65AE14EA52AF6B2667CBF998B379756B5597E |
| SHA384 | 430685FE17A7E0182F59F4D3416604700D2843C89E22291A6A36E2FB648745FF814127663F6EA36B371D049B527309AC |
| SHA512 | 7CFEFDBD58039694657FA23F0D5C150C026FC3F007DD7E40F853CF78B2101B5943D9E452A4F6291FB2567C8F69C946C4193BFB8B604356069AB1E382609B9A9C |
| SSDEEP | 49152:MoSbtAyjXQ52sKplatxaix287JaOB/i+OYOOrm:Mo357t8Ybry |
Runtime Data
Window Title:
Command Line Options - Everything
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (RW-) C:\Users\user\Documents | File |
| (RW-) C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.19041.1_none_b555e41d4684ddec | File |
| \BaseNamedObjects__ComCatalogCache__ | Section |
| \BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \BaseNamedObjects\windows_shell_global_counters | Section |
| \Sessions\1\BaseNamedObjects\windows_shell_global_counters | Section |
| \Sessions\1\Windows\Theme4048709601 | Section |
| \Windows\Theme603176458 | Section |
Loaded Modules:
| Path |
|---|
| C:\program files\Everything\Everything.exe |
| C:\Windows\System32\ADVAPI32.dll |
| C:\Windows\System32\bcryptPrimitives.dll |
| C:\Windows\System32\combase.dll |
| C:\Windows\System32\comdlg32.dll |
| C:\Windows\System32\GDI32.dll |
| C:\Windows\System32\gdi32full.dll |
| C:\Windows\SYSTEM32\iertutil.dll |
| C:\Windows\System32\IMM32.dll |
| C:\Windows\SYSTEM32\kernel.appcore.dll |
| C:\Windows\System32\KERNEL32.DLL |
| C:\Windows\System32\KERNELBASE.dll |
| C:\Windows\System32\msvcp_win.dll |
| C:\Windows\System32\msvcrt.dll |
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\System32\ole32.dll |
| C:\Windows\System32\RPCRT4.dll |
| C:\Windows\System32\sechost.dll |
| C:\Windows\System32\shcore.dll |
| C:\Windows\System32\SHELL32.dll |
| C:\Windows\System32\SHLWAPI.dll |
| C:\Windows\System32\ucrtbase.dll |
| C:\Windows\SYSTEM32\urlmon.dll |
| C:\Windows\System32\USER32.dll |
| C:\Windows\system32\uxtheme.dll |
| C:\Windows\System32\win32u.dll |
| C:\Windows\System32\WS2_32.dll |
| C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.19041.1_none_b555e41d4684ddec\COMCTL32.dll |
Signature
- Status: Signature verified.
- Serial:
0554D03D517345589F62CA21C7789A22 - Thumbprint:
D729CE691A8FC342ED6B0F607C7457B05B5AACF9 - Issuer: CN=DigiCert SHA2 Assured ID Code Signing CA, OU=www.digicert.com, O=DigiCert Inc, C=US
- Subject: CN=voidtools, O=voidtools, L=Wilmington, S=South Australia, C=AU
File Metadata
- Original Filename: Everything.exe
- Product Name: Everything
- Company Name: voidtools
- File Version: 1.4.1.988
- Product Version: 1.4.1.988
- Language: English (United States)
- Legal Copyright: Copyright 2020 voidtools
Possible Misuse
The following table contains possible examples of Everything.exe being misused. While Everything.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | proc_creation_lnx_network_service_scanning.yml | - '/telnet' # could be wget, curl, ssh, many things. basically everything that is able to do network connection. consider fine tuning |
DRL 1.0 |
| sigma | registry_event_asep_reg_keys_modification_currentversion.yml | - 'C:\Program Files\Everything\Everything.exe' |
DRL 1.0 |
| atomic-red-team | T1098.001.md | # in the context of an ART test (and not a real attack), we don’t need to keep access for too long. In case the cleanup command isn’t called, it’s better to ensure that everything expires after 1 day so it doesn’t leave this backdoor open for too long | MIT License. © 2018 Red Canary |
| atomic-red-team | T1114.001.md | Search through local Outlook installation, extract mail, compress the contents, and saves everything to a directory for later exfiltration. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1176.md | <blockquote>Adversaries may abuse Internet browser extensions to establish persistent access to victim systems. Browser extensions or plugins are small programs that can add functionality and customize aspects of Internet browsers. They can be installed directly or through a browser’s app store and generally have access and permissions to everything that the browser can access.(Citation: Wikipedia Browser Extension)(Citation: Chrome Extensions Definition) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1548.002.md | REM will tell it to ignore everything after %windir% and treat it just as a NOTE. Therefore just executing cmd with admin privs. | MIT License. © 2018 Red Canary |
| signature-base | airbnb_binaryalert.yar | $s3 = “-cmdfile local.bat #will execute everything from local.bat” ascii wide | CC BY-NC 4.0 |
| signature-base | apt_eqgrp.yar | $s4 = “Not everything is set yet” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_eqgrp_apr17.yar | $x4 = “[!] nothing looks vulnerable, trying everything” fullword ascii | CC BY-NC 4.0 |
MIT License. Copyright (c) 2020-2021 Strontic.